Tag security
Post details
"If your computer has a Thunderbolt port, an attacker who gets brief physical access to it can read and copy all your data, even if your drive is encrypted and your computer is locked or set to sleep." tl;dr: stop using computers. ¯\_(ツ)_/¯ thunderspy.ioMattias Geniar (@mattiasgeniar)Mon, 11 May 2020 07:17 +0000
Post details
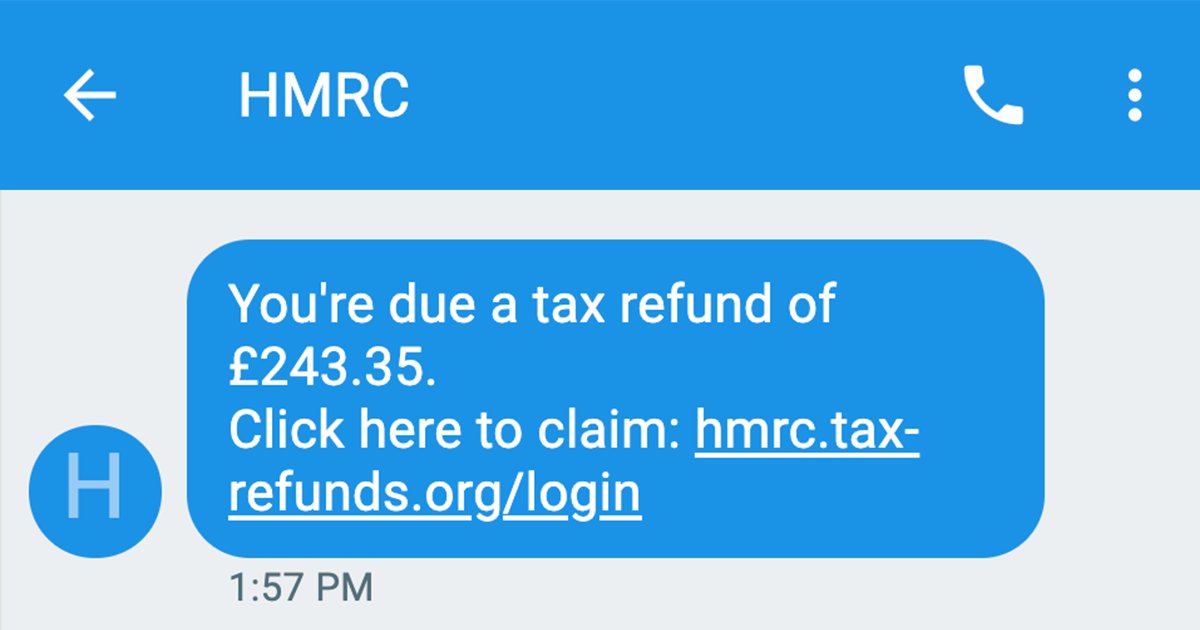
Ever got a text like this? It doesn't necessarily look dodgy. But if you know what to look for, you'll see it has all the hallmarks of a scam 👀 Let's break it down (thread) 👇Monzo (@monzo)Thu, 07 May 2020 13:40 +0000
Post details
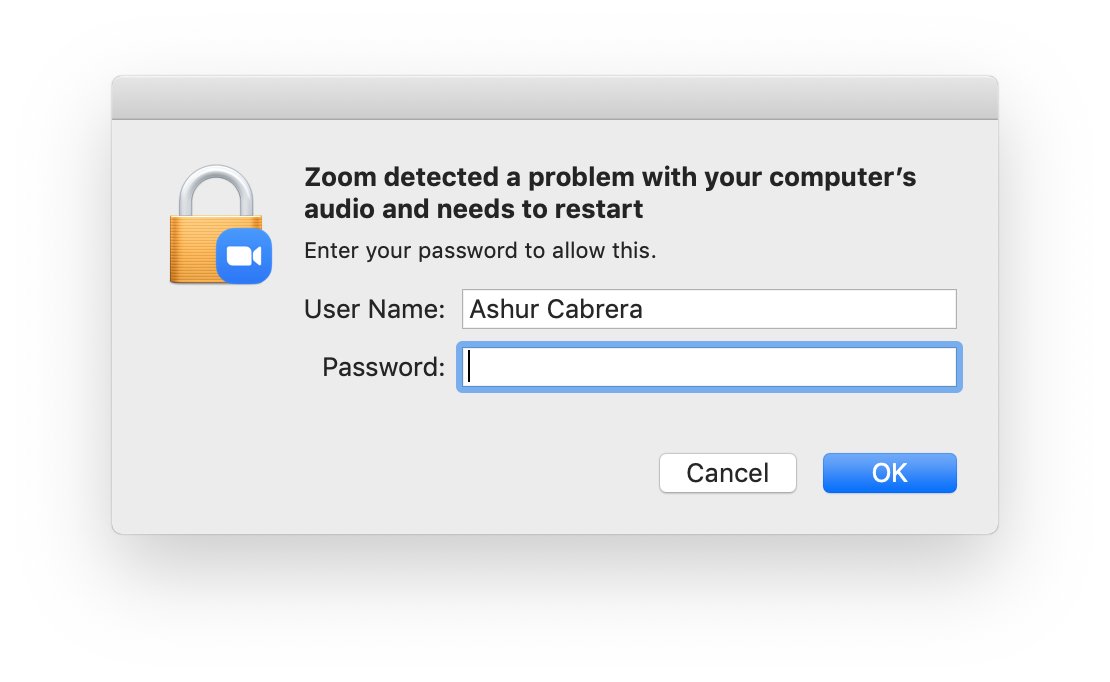
Zoom just did this to an engineer at our company. Not cool. So not cool. Deceptive and shady AF. Count the security dark patterns here...
Post details
wyd @zoom_usAshur Cabrera 😷 (@ashur)Thu, 26 Mar 2020 16:32 GMT
Liz Fong-Jones (方禮真) (@lizthegrey)Fri, 17 Apr 2020 22:09 +0000
Tomcat May Log Cookies Out-of-the-Box (3 mins read).

Warning you about cookies being logged out-of-the-box, and how to resolve it.
An interesting look at how using one key for everything (SSH to servers, SSH for git hosting, etc) can be a Bad Thing™
Piping Data When Not Running a Command with sudo (1 mins read).
How to (more) safely pipe stdin to an elevated command with sudo tee.
DevOpsDays London 2019 (63 mins read).

A writeup of the DevOpsDays London conference, and the talks and Open Spaces I attended.
This is a really interesting post to hear how some other folks in a similar environment to us manage their secrets.
It's always cool to see how other folks are doing similar things, anyway, and as usual, Monzo have a great blog post.
This is a really interesting article about the flaws in PGP - I don't have enough security backing and understanding to argue it, but it sounds legitimate. It's a surprise this isn't being talked about more if it is as bad as it is
I found this when listening to episode 194 of the Bike Shed podcast: My PGP Shame. I'd only added this episode to my playlist as it was an interesting title, but listening to it, it was even better than I thought.
There was some great stuff in there about Thoughtbot's application security guide, linked, which is a definite must-read.
My favourite quote of the episode, though, is the following exchange:
I've got to be honest, how does anything work at all? Oh computers don't work
Cyber Nottingham May (5 mins read).
A writeup of the Cyber Nottingham meetup in May.
This is a great writeup about how to harden your SSH setup using 2-factor authentication. Would really recommend it!
You're currently viewing page 5 of 5, of 239 posts.