Post details
May the 4th be with you! Brand new OAuth shirts just launched: "I find your lack of security disturbing" Available in a variety of styles and also as a hacker hoodie! …

May the 4th be with you! Brand new OAuth shirts just launched: "I find your lack of security disturbing" Available in a variety of styles and also as a hacker hoodie! …

We implemented OAuth for the 50 most popular APIs. TL;DR: It is still a mess.

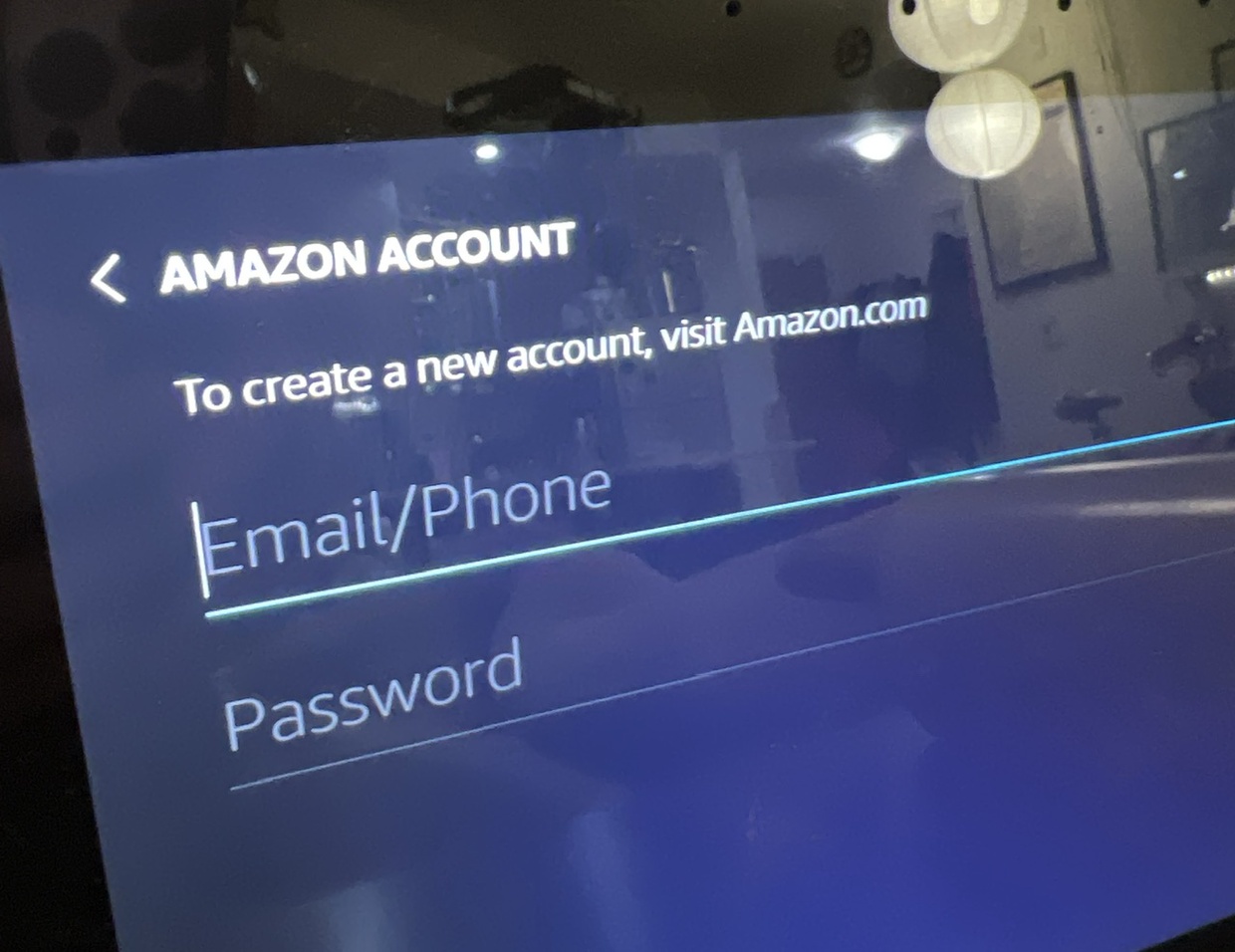
It's been a while since I've set up an Amazon Echo device. Do I need to come over there and teach some Amazon folks about the OAuth Device Flow? There is a better way than making me type my password …
OAuth 1.0 client package for Go. Contribute to gomodule/oauth1 development by creating an account on GitHub.
Yes to variable expiry, but on refresh tokens not access tokens. Access tokens should always be short lived to the point you don't care. But stick it on the refresh token (or make it standard to allow no refresh at all, so it expires after that first hour) - that'd be cool!Steven Pears (@StevenPears)Wed, 26 Jan 2022 16:51 GMT
I wrote this 11 years ago. shkspr.mobi/blog/2011/01/o… I really wish more OAuth services would use the `expires_in` response. It would be great if you could authorise a service for a specified and limited amount of time.Terence Eden (@edent)Wed, 26 Jan 2022 16:13 GMT
oauth, but for zoomers
💾😺 #1 webring stan ⟦ prev | random | next ⟧ (@GalacticFurball)Mon, 22 Nov 2021 23:23 GMT
Why You Should Avoid using Client Secret Authentication for OAuth2 Client Credentials (7 mins read).

Why I recommend against using client secret authentication for OAuth2 and OpenID Connect APIs.
Tumblr's API is now OAuth2: engineering.tumblr.com/post/666127838… A significant security upgrade from what they had used previously (OAuth1.0a), let's see if @twitterdev will catch up to the @tumblr team.Emelia 👸🏻 (@ThisIsMissEm)Wed, 27 Oct 2021 15:47 +0000
I couldn't find a comprehensive illustration to explain PKCE with OAuth so I made one myself! Pretty happy with how it turned out, what do you think?Kadi Kraman (@kadikraman)Sun, 08 Mar 2020 01:36 GMT
You're currently viewing page 1 of 1, of 29 posts.