Setting up govulncheck in GitHub Actions with GitHub Code Scanning alerts

With oapi-codegen, as many other folks in the ecosystem, we've been asked a few times in the past "can you please update this dependency as it has a CVE".
I'll generally reach for govulncheck as a way to confirm the impact, given it validates - via static analysis - whether the dependency is actually called as part of your operation (sometimes known as "reachability").
Although we're still working towards defining when dependencies with CVEs will be updated, this is a step towards being able to have a better gauge over what's impacted and when.
As a step further from Brandur's thoughts on running govulncheck in CI, we can go a step further to integrate the results into GitHub Code Scanning alerts, for better visibility.
For instance, when running against the "runtime" library, we can see:
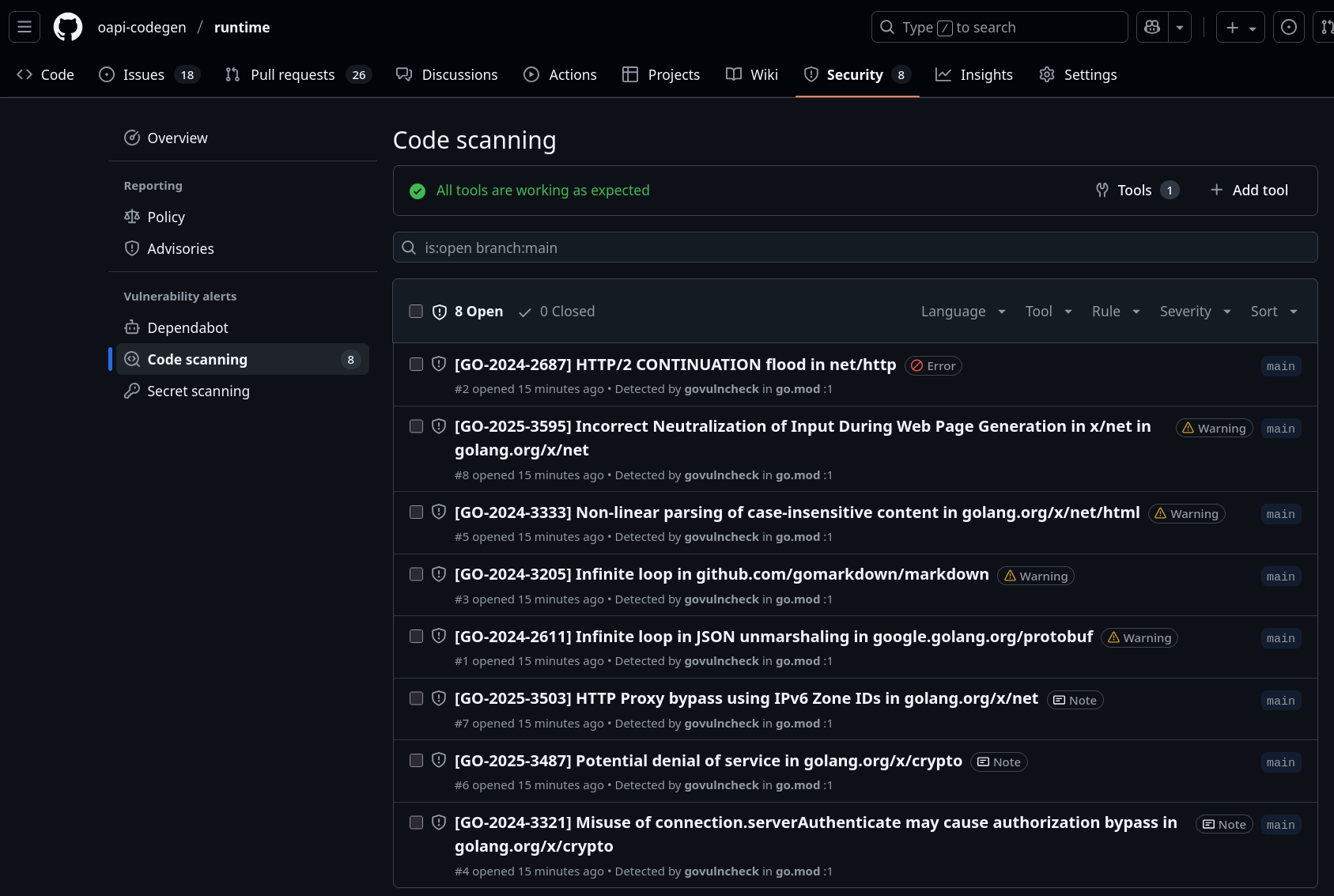
So how do we do this?
I've found that the following GitHub Actions workflow is the minimal set of configuration needed to get govulncheck's SARIF reporting format out, and then uploaded into GitHub to surface as a Code Scanning alert:
name: Determine known CVEs through `govulncheck`
on:
push:
branches:
- main
schedule:
# Mondays at 0000
- cron: "0 0 * * 1"
jobs:
check-for-vulnerabilities:
name: Check for vulnerabilities using `govulncheck`
runs-on: ubuntu-latest
permissions:
security-events: write
contents: read
steps:
- uses: golang/govulncheck-action@b625fbe08f3bccbe446d94fbf87fcc875a4f50ee # v1.0.4
with:
# NOTE that we want to produce the SARIF-formatted report, which can then be consumed by other tools ...
output-format: sarif
output-file: govulncheck.sarif
# ... such as the Code Scanning tab (https://github.com/oapi-codegen/oapi-codegen/security/code-scanning?query=is%3Aopen+branch%3Amain+tool%3Agovulncheck)
- name: Upload SARIF file
uses: github/codeql-action/upload-sarif@192325c86100d080feab897ff886c34abd4c83a3 # v3.30.2
with:
sarif_file: govulncheck.sarif
category: govulncheck
