Post details
A star of “The Office” comes to our office to answer your most pressing questions about tech.

A star of “The Office” comes to our office to answer your most pressing questions about tech.

Pedro Pascal proves that sometimes the most masculine thing to do is to be vocally and unflinchingly supportive of vulnerable people.
In this episode of the Distributed podcast features Matt Wynne, staff software engineer at Mechanical Orchard and a longtime advocate for Agile and Behavior-Driven Development (BDD)

In this heartfelt and inspiring episode of 99 Dev Problems, host Tessa Kriesel chats with the multifaceted Kevin Blanco, a DevRel advocate, film enthusiast, and tech professional from Costa Rica. Kevin shares his remarkable journey from humble beginnings, discovering computers in high school, to becoming a passionate community builder and a creative force in developer advocacy.Topics covered include:Community Power: Kevin highlights how the Drupal community's generosity shaped his career and emphasizes the importance of giving back to the communities that uplift us.From Developer to Advocate: Transitioning from a 15-year tech engineering role to DevRel, Kevin discusses how his love for storytelling and creativity aligns with his work at AppSmith, an open-source low-code platform.Creative Approach to DevRel: Kevin reveals his process of blending film school storytelling techniques into developer advocacy, focusing on empathy-driven video content, user empowerment, and building meaningful partnerships.Lessons in Simplicity: The duo explore the pitfalls of overengineering and the virtues of simplicity, shedding light on practical solutions to achieve business goals.Inspiration and Uniqueness: Kevin shares profound advice on creativity, personal growth, and embracing one's unique journey, offering actionable insights for developers and tech enthusiasts at every level.Join us for this insightful conversation that bridges tech, creativity, and community, showcasing how authenticity and passion can drive both personal and professional success.Where to Find Kevin Blanco:LinkedInKevinBlanco.devYouTube

In this engaging episode of 99 Dev Problems, host Tessa Kriesel welcomes guest, Amy Dutton, a seasoned web developer with 24 years of experience. Amy shares her journey from starting web development at 16 to becoming the lead maintainer of RedwoodJS. The conversation touches on her evolution from design to development, her early career experiences, and her latest ambitious project, Build Twelve—a year-long challenge to develop 12 projects in 12 months.Amy dives deep into the tech stacks and decision-making processes behind her projects, including her experiences with Laravel and Next.js, as well as the complexities of framework development. She also discusses the challenges of balancing technical work with building and maintaining a community, particularly in her Part-Time Startup initiative.The two share insights on getting unstuck as developers, leveraging AI tools like Claude and ChatGPT, and balancing the desire for perfection with the need for progress. Amy highlights the importance of walking away when stuck and embracing tools and workflows that play to individual strengths.This episode is packed with valuable lessons for developers at every stage, from overcoming technical hurdles to balancing the human and technical aspects of community-building.Where to Find Amy DuttonTwitter/X: @SelfTeachMeWebsite: buildtwelve.com – Subscribe for project updates and insights.Podcast: Compressed.fmTune in to hear Amy’s inspiring journey and practical advice, and stay connected for future collaborations and insights!

Lessons from 100+ DevTool founders - DevTools successes, failures and stories in a free weekly email and podcast.

I will be attending
Lessons from 100+ DevTool founders - DevTools successes, failures and stories in a free weekly email and podcast.

Lessons from 100+ DevTool founders - DevTools successes, failures and stories in a free weekly email and podcast.

Lessons from 100+ DevTool founders - DevTools successes, failures and stories in a free weekly email and podcast.

Lessons from 100+ DevTool founders - DevTools successes, failures and stories in a free weekly email and podcast.

Lessons from 100+ DevTool founders - DevTools successes, failures and stories in a free weekly email and podcast.

Lessons from 100+ DevTool founders - DevTools successes, failures and stories in a free weekly email and podcast.

Listen to Ep 294: Carey Mulligan from Off Menu with Ed Gamble and James Acaster. Three-time Oscar nominee Carey Mulligan – star of Tim Key and Tom Basden’s ‘The Ballad of Wallis Island’ – is this week’s dream guest. But can James name those nominated roles? Carey Mulligan stars in ‘The Ballad of Wallis Island’ which is in cinemas from 30 May. Off Menu is a comedy podcast hosted by Ed Gamble and James Acaster.Produced, recorded and edited by Ben Williams for Plosive.Video production by Megan McCarthy for Plosive.Artwork by Paul Gilbey (photography and design).Follow Off Menu on Twitter and Instagram: @offmenuofficial.And go to our website www.offmenupodcast.co.uk for a list of restaurants recommended on the show.Watch Ed and James's YouTube series 'Just Puddings'. Watch here.

Listen to Ep 274: Andy Zaltzman (Christmas Special) from Off Menu with Ed Gamble and James Acaster. Joining us for a Christmas Special second helping is ‘Taskmaster’ champion and ‘The Bugle’ podcast, Andy Zaltzman.Andy Zaltzman is on tour now with ‘The Zaltgeist’, running until 9th May 2025 at London's Leicester Square Theatre. For full dates and tickets, visit www.andyzaltzman.co.ukFollow Andy on Twitter @ZaltzCricket Off Menu is a comedy podcast hosted by Ed Gamble and James Acaster.Recorded and edited by Ben Williams for Plosive.Artwork by Paul Gilbey (photography and design) and Amy Browne (illustrations).Follow Off Menu on Twitter and Instagram: @offmenuofficial.And go to our website www.offmenupodcast.co.uk for a list of restaurants recommended on the show.Watch Ed and James's YouTube series 'Just Puddings'. Watch here.


What's the difference between Renovate's depName and packageName? (3 mins read).

What the differences are, and where you may want to use one or the other.
i had some really stressful interactions on github yesterday and today. lets just remember many of us are doing this OSS work for free and to do good, kindness is appreciated
Was very honoured to be featured as part of #MaintainerMonth for the Open Source Initiative's view into Open Source maintainers and their experiences, and being able to share my own experiences on opensource.org :purple_heart:
My experience as a maintainer (8 mins read).
A guest post for opensource.org, about my experience as a maintainer, as part of 2025's Maintainer Month.
Lessons from 100+ DevTool founders - DevTools successes, failures and stories in a free weekly email and podcast.

Creating nested fenced code blocks with Hugo (1 mins read).
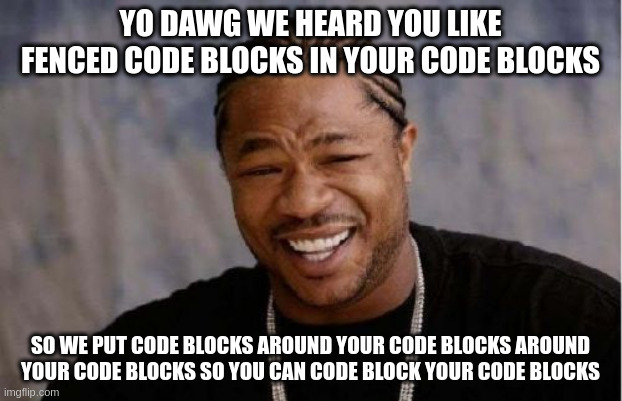
How to write a Markdown file with a fenced code block, which includes another code block inside it.
Taking more control over your Cobra CLI documentation (2 mins read).

Releasing a library to manage the generation of Cobra CLI documentation using text/templates.
Setting up SSH key signing with Git (1 mins read).

How to sign your Git commits, using SSH keys.
I recently had a chat with Kairo about a project he maintains called Repository Service for TUF (RSTUF). We explain why TUF is tough (har har har), what RSTUF can do, and some of the challenges around securing repositories. The show notes and blog post for this episode can be found at

Lessons from 100+ DevTool founders - DevTools successes, failures and stories in a free weekly email and podcast.

Week Notes 25#19 (3 mins read).
What happened in the week of 2025-05-12?
After 25 years in tech it’s hard not to coast. Adriana has come from writing word docs for the ops team to deploy software, through Devops, and now has a focus on OTel and Kubernetes. How do we get more people from 100 to 400 levels and why is there no content in between? And why we need junior...

Improving the experience of browsing Renovate debug logs (4 mins read).

Creating a Terminal User Interface (TUI) application to improve the debugging experience with Renovate's debug logs.
Marianne, author of Kill It with Fire, and Greg join host Richard to dive into their new paper, “10 Quick Tips for Making Your Software Outlive Your Job.”

Go Meetup in San Francisco - Sponsored by Elastic & Cup o' GoIan Lance Taylor leaves the Go teamBlog: wget to Wipeout: Malicious Go Modules Fetch Destructive PayloadBlog: Security: The Habits That Matter Most by Christoph Berger⚡ Interview with Kevin Hoffman of SparkLogsSparkLogs.comSparkLogs on...

Derek Collison — creator of NATS and Co-founder & CEO of Synadia — joins the show to dive into the origins, design, and evolution of NATS, a high-performance, open-source messaging system built for modern cloud-native systems and part of the CNCF. Derek shares the story behind NATS, what makes it unique, and unpacks th...
😮💨

dipshits in 2019: you people are NPCs, you don't even think for yourselves dipshits in 2025: I have outsourced my thinking to Clippy
Sami talks with Tom Akehurst, Co-Founder of WireMock, about the delay and disconnect between front and back end development and how WireMock set out to bridge the two together.

William Woodruff discussed his project, Zizmor, a security linter designed to help developers identify and fix vulnerabilities within their GitHub Actions workflows. This tool addresses inherent security risks in GitHub Actions, such as injection vulnerabilities, permission issues, and mutable tags, by providing static analysis and remediation guidance. Fresh off the heels of the tj-actions/changed-files backdoor, this is a great topic with some things everyone can do right away. The show notes and blog post for this episode can be found at

Looking back at oapi-codegen's last year (6 mins read).

A recap of oapi-codegen's last year, in light of it being Maintainer Month, and continuing to ask for sponsorship.
What's in the SOSS? features the sharpest minds in security as they dig into the challenges and opportunities that create a recipe for success in making software more secure. Get a taste of all the ingredients that make up secure open source ...

Thanks for listening. Check out all the links to all the things at https://cupogo.dev/.GCC 15.1 Released With Support For COBOLos: Root permits access to parent directoryGOOS=noneThe "most ergonomic" config libraryGo Meetup in San Francisco - Sponsored by Elastic & Cup o' GoLinkedIn...

Kaizen 19 has arrived! Gerhard has been laser-focused on making Jerod's pipe dream a reality by putting all of his efforts into Pipely. Has it been a big waste of time or has this epic side quest morphed into a main quest?!
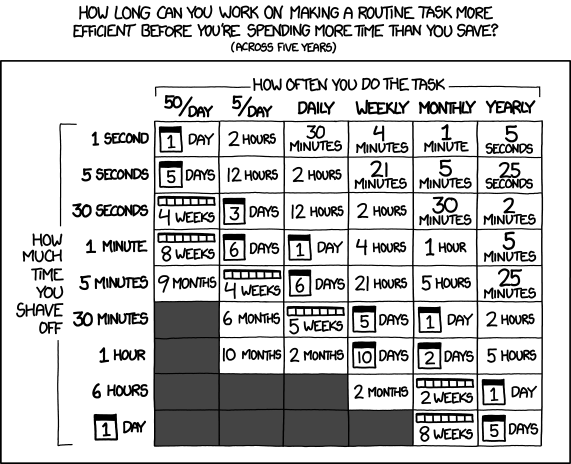
Automating things, even when it doesn't save time, is how you learn the skills to automate the things that will.
Overriding a Gradle project property which has . and _ characters, without modifying the buildscript (4 mins read).

How to use GRADLE_OPTS to safely override a Gradle property (with special characters in its name) without modifying the buildscript.