Post details
5,979 votes and 810 comments so far on Reddit

5,979 votes and 810 comments so far on Reddit

Attached: 1 video Welp, Substack Notes has set a new record for fastest time to me to leave a platform after joining. Libertarian tech bros say no to racism challenge, difficulty: impossible

Content warning: ST:Picard S3E9 "Vox" spoilers
Ok HELLO I’m going to try to actually be active on here 👋🏼 esp bc there are so many of you that I miss dearly 🥲 What to expect: 🗞️ Articles I’ve written 🍑 Fun research findings 🚽 Mirror selfies 🏳️🌈 My cute queer relationship 🌱 Random learnings 🎤 Events I’m at or covering 🤐 Thoughts I can’t say irl in the office 🛸 Probably other things idk Some might crossover from Twitter while I’m still getting used this platform, but let’s see 👀
A GitHub action to generate a stackaid.json file based on your repository's dependency graph - GitHub - stackaid/generate-stackaid-json: A GitHub action to generate a stackaid.json file based o...
Attached: 1 image Your jest tests are (probably) wrong. Add this to your jest config to prevent leaking state between tests. #jest #javascript #typescript #testing #unittest

If anyone ever texts you "We need to talk" text them back with "Yes we certainly do" so that they feel stressed also.
i'll say it again, fascists go after small, marginalized minorities bc doing so gives them an opportunity to establish precedent for broad, invasive powers against citizens in a way they don't think the mainstream will fight back against once those laws are established, they won't be used JUST against us marginalized folks
A while ago, I wrote a little about what to include in a README for a project (https://matthiasott.com/notes/how-to-readme). I now also created and published a README template I’ll use in upcoming projects. I hope it is useful! Any contributions or corrections are very welcome. 🤗 https://github.com/matthiasott/README-template
There was a lot of press about the nasty environmental impact of cryptocurrency (all of it definitely valid!). But it also makes me wonder the same about AI, especially big publicly-accessible ones like GPT - GPUs and accelerators draw a lot of power, not to mention e-waste generated by inexonerable technological advancement, and I don't really see anyone talking about it. Maybe it's a non-issue, I don't know much about how these things work in the background, but surely it's noticeable?
Nóva's law of principal architecture review documentation. In a sufficiently large organization the number of pages in a Google doc is roughly equal to the number of people who will disagree with you either publicly or privately. The only way to ensure your ideas will be accepted and supported broadly is to achieve absolute 0 and never write a doc. If your ideas are too complicated to communicate "at runtime" via audio/text/email or otherwise it will never be accepted broadly by the org.
Generates Go (golang) Structs from JSON schema. Contribute to elastic/go-json-schema-generate development by creating an account on GitHub.
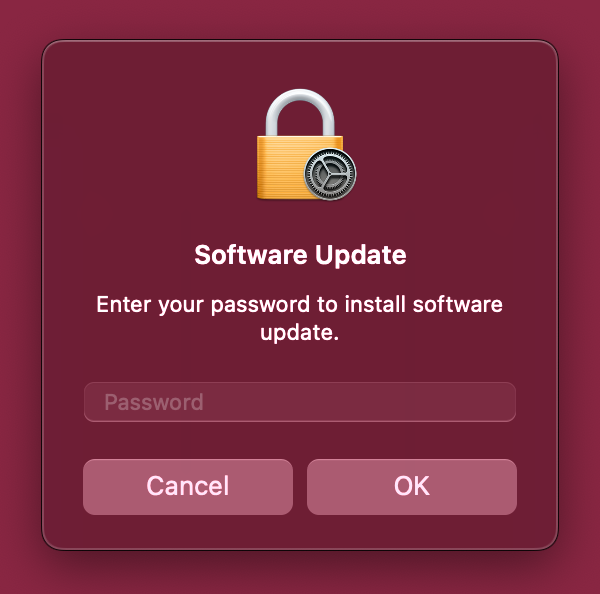
Attached: 1 image I wish Apple would stop doing pop-ups asking for my password without providing any opportunity to get details on which update it's prompting me to approve. It feels like this is training users to put their passwords in arbitrary pop-ups and leads to users more open to phishing attacks.
Attached: 1 image this still makes me unnecessarily angry

New Planet Earth episode just dropped
Tofte | Christopher Polt 🏳️🌈 (@CBPolt)Mon, 10 Apr 2023 02:44 +0000
Extension handlers for the slog library. Contribute to galecore/xslog development by creating an account on GitHub.
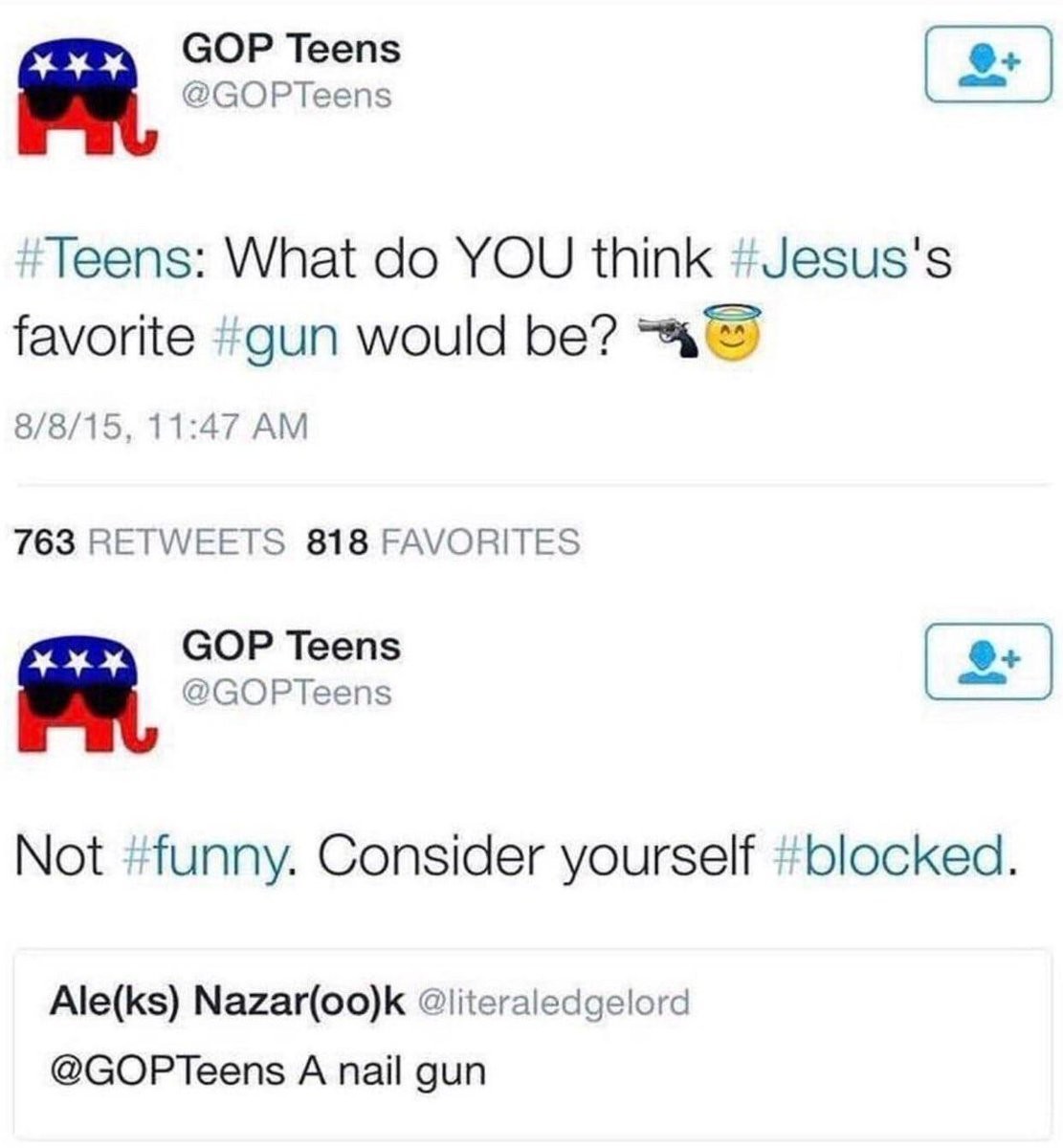
Attached: 1 image If you're going to give a legitimately right answer and still get blocked... --- RT @OneRadChee https://twitter.com/OneRadChee/status/1645117246073602049
stop maintaining software
David Buchanan (@David3141593)Sun, 09 Apr 2023 17:26 +0000
Idk who needed to hear this but I’m pansexual AF 🌈 like rly queer, like rly hella gay. Also helloJessica Crosby (@Jhyp3)Sun, 09 Apr 2023 19:15 +0000
lmao all thanks go to my adhd medication
ely kreimendahl (@ElyKreimendahl)Sat, 08 Apr 2023 18:49 +0000
sexually I’m a bottom, but administratively I’m a top (pays the bills, opens mail, makes appointments)
ely kreimendahl (@ElyKreimendahl)Sat, 08 Apr 2023 18:40 +0000
someone on Tiktok just called this a “PowerPoint bottom” and I am deceased 😭😭😭😭
ely kreimendahl (@ElyKreimendahl)Sun, 09 Apr 2023 12:53 +0000
i.e. a power bottom, especially when it comes to picking up paper towels
ely kreimendahl (@ElyKreimendahl)Sat, 08 Apr 2023 18:43 +0000
Channel 5 has put the wrong subtitles on Ben Hur! It is hilarious!!
Professor Graham Williams (@ProfGAWilliams)Sat, 08 Apr 2023 09:52 +0000
me: god, why must you give me your hardest battles god: i don't. you are my weakest soldier and these battles are so easy. it's an email why are you cryingShelf (@shelfcomedy)Thu, 30 Sep 2021 09:27 +0000
Remember, friends, you can't spell 'Python' without 'y tho'
Easy, cheap labour rights improvement which will never happen: require employers to tell employees how much their salary has changed, in real terms, every year.
I am losing the will to live after spending the whole day filling in visa renewal forms 😪
is there any website or app that brings you joy? pls share minimum requirement: it must not reek of capitalism (i.e. shouldn't try to immediately sell me shit or shove cookies/ads in my face) extra points if: - it's accessible - it doesn't require auth - you actually use it frequently - the person who made it is on this site (tag them)
Life with a dog is about 90% following each other around and wondering what the other is eating.
non aesthetic things (@PicturesFoIder)Sat, 08 Apr 2023 19:08 +0000
A few thoughts on GitHub’s practice of keeping their code synchronized with Rails <code>main</code>.
Attached: 1 image So, as some of you may know, I was on the #Twitter Developers "Insiders" programme in the before times. As part of that, they occasionally sent me branded swag as a thank-you gift. Insiders would regularly get different things sent to them. I didn't know how highly esteemed they held me until I saw this sticker on the delivery box...!

Attached: 1 image Did you ever watch Robot Wars and think… “I could do that!”? Well now’s your chance to try! Come and join us at Nottingham Hackspace on the 6th of May to build and fight your own robot with help from experienced builders. Open to general public and members, as long as you are 18 or over 🙂 #Robotics #Nottingham https://www.eventbrite.co.uk/e/antweight-combat-robotics-workshop-tickets-611516431107

313K Likes, 1,206 Comments - Karen Gillan (@karengillan) on Instagram: "This Barbie is a cyborg and MIGHT kill you #gotgvol3"

YOLO in this case meaning "You Only Lend Oh my god these interest payments are killing me, someone please pay me for this site, agh."
Marley Jay (@MarleyJayBiz)Thu, 06 Apr 2023 16:26 +0000
For a guy who has racked up so many recent Ls, it is crazy that he is just getting rid of the only W he had
Matt McGillvray (he/him) (@MattMcGillvray)Thu, 06 Apr 2023 15:15 +0000
Since the beginning, GitHub.com has been a Ruby on Rails monolith. Today, the application is nearly two million lines of code and more than 1,000 engineers collaborate on it daily. We deploy as often as 20 times a day, and nearly every week one of those deploys is a Rails upgrade. Upgrading Rails weekly Every […]

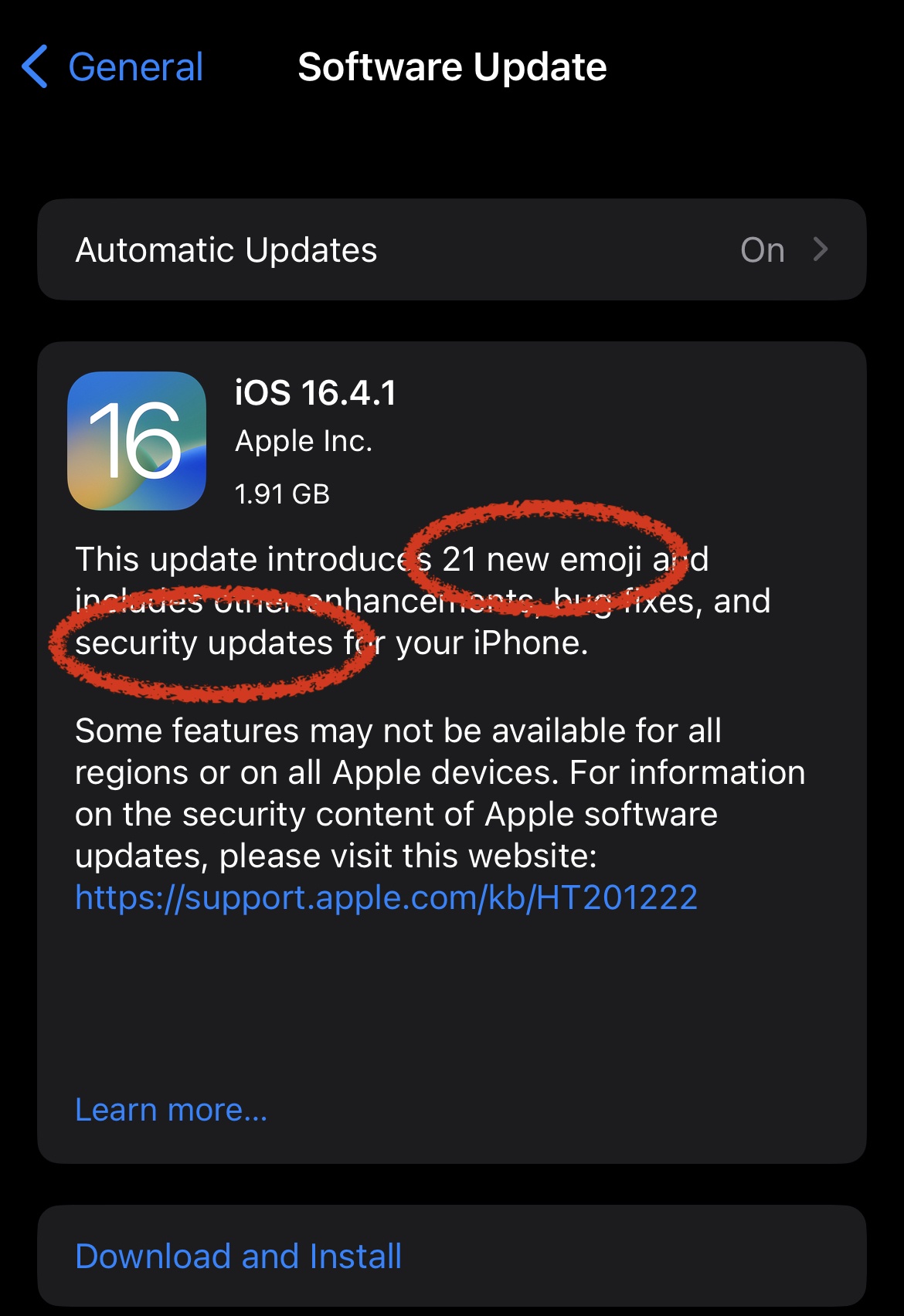
we all know the real reason you install iOS updates 👀 p.s. go update your devices
Content warning: The Mandalorian S3E6
Took one of them autism quotient self-tests and I got 34 out of a possible 50. I wonder if I get any bonus points for the number of times I went "this question needs more context before I can answer it properly."
Matthias Ott is an independent user experience designer and developer from Stuttgart, Germany. Besides design practice he teaches Interface Prototyping at the Muthesius Academy of Fine Arts and Design, Kiel.