Post details
Sometimes I forget that I'm tweeting to 16k.
Josie (@javavvitch)Mon, 13 Feb 2023 14:49 GMT
Sometimes I forget that I'm tweeting to 16k.
Josie (@javavvitch)Mon, 13 Feb 2023 14:49 GMT
As a committer on a couple of medium-popularity projects I couldn't agree more with this: "Maintaining a successful open source project is Good Will Hunting in reverse. You start out as a respected genius, and end up being a janitor who gets into fights." — Byrne Hobart (@ByrneHobart@twitter.com)
When Microsoft leadership feels like GitHub layoffs are not bad enough, they have to increase the pain by forcing people to use MS Teams on their 4y old laptops.
Karri Saarinen (@karrisaarinen)Fri, 10 Feb 2023 01:34 GMT
When I share how horrible it is to be left for dead as a medically vulnerable person in the prime of my life people feel sorry for me & say it's unfair When I point out that not masking in public is what's leaving me for dead - I'm hysterical, crying victim & asking for the moonJolenta Greenberg (@JolentaG)Mon, 13 Feb 2023 17:51 GMT
tech workers should be very quickly realizing why they need a union right about now
Post details
imagine doing a stock buyback in between two rounds of layoffs, i have some ideas about what should happen to Facebook execs but i can't post them on twitter dot com twitter.com/cubefag/status…Cara Esten (@caraesten)Mon, 13 Feb 2023 15:40 GMT
Janus Rose (@janusrose)Mon, 13 Feb 2023 15:43 GMT
imagine doing a stock buyback in between two rounds of layoffs, i have some ideas about what should happen to Facebook execs but i can't post them on twitter dot com
Post details
nope reuters.com/technology/met…
hayes 🧶 (@cubefag)Mon, 13 Feb 2023 15:38 GMT
Cara Esten (@caraesten)Mon, 13 Feb 2023 15:40 GMT
tech jobs were considered cushy and “safe” until very recently and it really just shows how the hammer inevitably comes down on everyone. organize your workplace now.
Janus Rose (@janusrose)Mon, 13 Feb 2023 15:46 GMT
Today is my last day at Twilio. I'm going to take some time before officially going on the job market, but if you have anything interesting for my skill set, my DMs are open! Take care of yourselves and each other 🤗Ian Coldwater (@IanColdwater)Mon, 13 Feb 2023 15:46 GMT
gatekeep gaslight guantanamo bay
Post details
Good afternoon from Camp Justice at Guantanamo Bay. Some visiting NFL cheerleaders got the Super Sunday festivities underway yesterday with a show during a weightlifting contest at the Navy base gym. The first war court hearing of the year is set for Tuesday.
Carol Rosenberg (@carolrosenberg)Sun, 12 Feb 2023 17:59 GMT
✨💎 Ruby Railed 💎✨ (@MxRubyRailed)Mon, 13 Feb 2023 16:04 GMT
(on a first date) yeah so if i had my own wario or waluigi i dont know if it would be called wazach or just wach, which would be pronounced "wack," but zachs and zacks are so different that i still wouldnt spell it with a k. you look beautiful tonight by the way. can i kiss you
zach silberberg (@zachsilberberg)Sat, 11 Feb 2023 16:49 GMT
Why the hell do I keep being asked to do this?

Yes! Absolutely hate this as a term 👏🏽
Between and I took 9985 steps.
idk about sports but i can give u some superb oral
violet valentine (top 2%) (@slutpilled)Mon, 13 Feb 2023 03:58 GMT
RIHANNA LOOK OUT
Patrick Monahan (@pattymo)Mon, 13 Feb 2023 01:46 GMT
yeah so sad that it got cancelled after 1 season. it had such potential
zach silberberg (@zachsilberberg)Sun, 12 Feb 2023 21:36 GMT
“what are you bringing to the party?” oh just my nervous energy
trash jones (@jzux)Sun, 12 Feb 2023 17:29 GMT
she’s a billionaiiiiirreeeeee — she don’t gotta sing and dance for y’all no mooooorreeeee
Scooter Taylor (@ScooterTaylor)Mon, 13 Feb 2023 01:46 GMT
Monacht! ⏳ (@MonachtVT)Sat, 11 Feb 2023 00:40 GMT
Week Notes 23#06 (5 mins read).
What happened in the week of 2023-02-06?
The @github merge queue public beta filled up basically instantly with Brits; queuing for access to a service that enables queuing is basically like catnip to those folks.Post details
HOLY SHIT FINALLY github.blog/changelog/2023…You are over the daily limit for sending tweets (@bitandbang)Wed, 08 Feb 2023 18:30 GMT
Corey Quinn / @quinnypig@awscommunity.social (@QuinnyPig)Thu, 09 Feb 2023 23:26 GMT
Reminder that a guillotine on a stage is the only platform nazis deserve.
trash, but make it fashion 🦝✨ (@ElleArmageddon)Sun, 12 Feb 2023 18:45 GMT
Oh just seen this part of the message, yeah I can deffo sort that specific issue today, I know what that is 👍🏼
Thanks yeah I saw they're not super great, will hopefully sort it soon 🤞🏽
# Hogwarts Legacy: So You Want to Separate the Art From the Artist So you placed your order for *Hogwarts Legacy* or are considering it. You know J.K. Rowling is a horrible person, or so you've heard, but you really want to enjoy your favourite books' latest game. Sure, she's a little odd when it comes to those trans people, but other than that, she's not all bad, right? Let me enjoy the game, you say, that doesn't mean I support her (the [obvious falsity](https://twitter.com/jk_rowling/status/1580639051774054404) of that aside), and really: what's wrong with it in the first place, huh? Well, hypothetical stranger I just made up, today is your lucky day! Since you asked… If you are unwilling to hear any arguments, this text is not for you, but if you ask 'what's the big deal anyway', you've come to the right place. Let's rewind a little. Until recently, J.K. Rowling was mostly a beloved fantasy author. There were always criticisms of her works (and I don't mean the frankly plebeian style), such as the fact that the goblins, [hook-nosed, hunched bankers with a love for plotting and betrayal](https://www.thejc.com/comment/comment/harry-potter-is-gringotts-picture-antisemitic-1.482785) reside in a building with a [star of david on the floor](https://twitter.com/SamHaft/status/1064232757805617152), the [hasty retcon of a singular Jewish character (with the most cliché name of 'Goldstein')](https://twitter.com/jk_rowling/status/544946669448867841?lang=en), the subplot about the [enslaved servants who love slavery and hate being freed](https://www.theguardian.com/books/2015/dec/24/harry-potter-race-muggles-black-hermione), and so on and so forth, but by and large, most people saw her as the author of their favourite books, and that was it. Since then, Rowling has come out in support of the current [genocidal](https://www.lemkininstitute.com/statements-new-page/statement-on-the-genocidal-nature-of-the-gender-critical-movement%E2%80%99s-ideology-and-practice) campaign against trans people, ostensibly out of concern for women's rights, despite the fact that [people she has supported](https://twitter.com/jk_rowling/status/1462758716684611597?lang=en) call anti-abortion crusaders ['fine people'](https://twitter.com/Docstockk/status/1540306147328024576), people on her side [sue rape crisis centers](https://unherd.com/2022/07/why-im-suing-survivors-network/), and of course [in spite](https://blogs.scientificamerican.com/voices/stop-using-phony-science-to-justify-transphobia/) of [all known science](https://www.scientificamerican.com/article/beyond-xx-and-xy-the-extraordinary-complexity-of-sex-determination/), in support of [disproven junk science](https://neurosciencenews.com/gender-dysphoria-myth-19878/), [going against](https://publications.aap.org/aapnews/news/19021/AAP-continues-to-support-care-of-transgender) [all major](https://www.ama-assn.org/press-center/press-releases/ama-states-stop-interfering-health-care-transgender-children) [scientific](https://www.apa.org/monitor/2018/09/ce-corner) [organisations](https://www.aap.org/en/news-room/news-releases/aap/2021/frontline-physicians-oppose-legislation-that-interferes-in-or-penalizes-patient-care/), and on the same side as [anti](https://www.vice.com/en/article/93yabp/covid-anti-vaxxers-mocking-trans-people-with-transvaxxite-videos)-[vaxxers](https://www.thepinknews.com/2022/10/01/graham-linehan-covid-transphobia-climate-change/), [far-right](https://nypost.com/2022/09/05/chicago-hospital-teams-with-schools-to-promote-sex-toys-to-kids/) [extremists](https://www.city-journal.org/chicago-childrens-hospital-partners-with-local-school-districts-to-promote-radical-gender-theory), [anti](https://www.thesocialreview.co.uk/2021/01/02/transphobia-and-antisemitism/)-[semites](https://blogs.timesofisrael.com/the-antisemitic-conspiracy-theories-fueling-transphobia/), [more anti-semites](https://chican3ry.medium.com/jk-rowling-gender-ideology-and-antisemitism-7dd043bad37b), [authors of murderous manifests](https://www.thenational.scot/news/19691745.bbc-scandal-lily-cade-calls-trans-women-executed/), and [desinformation oligarchs](https://www.aidsmap.com/news/may-2021/whos-financing-anti-gender-movement-europe). It is no coincidence that [Rowling's public conversion into an avid transphobe](https://www.glamour.com/story/a-complete-breakdown-of-the-jk-rowling-transgender-comments-controversy) corresponds closely with the [skyrocketing of anti-trans bills](https://www.them.us/story/anti-trans-lgbtq-legislation-2023-new-laws), going from [60 bills in 2020 to 131 in 2021](https://www.washingtonpost.com/lifestyle/2022/10/14/anti-trans-bills/), making 2021 [the worst year at the time](https://www.hrc.org/press-releases/2021-officially-becomes-worst-year-in-recent-history-for-lgbtq-state-legislative-attacks-as-unprecedented-number-of-states-enact-record-shattering-number-of-anti-lgbtq-measures-into-law), and further to a staggering [120 bills in three weeks](https://www.aclu.org/press-releases/over-120-bills-restricting-lgbtq-rights-introduced-nationwide-2023-so-far) in early 2023 alone (that would be 2305 bills this entire year, if kept up)! So far, so awful. But since you're reading this, that is obviously not enough to convince you, so allow me to present further arguments. Let's talk about *Hogwarts Legacy*. Let's start with the fact that [Warner Brothers knowingly hired](https://kotaku.com/hogwarts-legacy-lead-designer-used-to-run-anti-social-j-1846316222) a [far-right gamergate youtuber](https://www.cbr.com/hogwarts-legacy-designer-alt-right/) as lead developer for the game, shortly after which details of the game were revealed, including the fact that [aforementioned antisemitic carricatures](https://www.dailydot.com/unclick/harry-potter-goblins-antisemitic-jon-stewart/) would be central to the plot, namely in the form of [a sinister plot and uprising](https://www.dailydot.com/unclick/hogwarts-legacy-goblins-antisemitism/) which includes [kidnapping a child](https://www.dailydot.com/unclick/hogwarts-legacy-antisemitism-goblins-horn/). Let me recap: the greedy, treacherous, hook-nosed bankers who hate regular wizards kidnap a child. If the words 'blood libel' – the belief that Jews steal children, a trope perpetuated in modern-day conspiracy theories about 'grooming' or 'woke indoctrination' – didn't mean anything to you: [now they do](https://www.adl.org/resources/glossary-term/blood-libel-false-incendiary-claim-against-jews). That this rebellion is motivated by the [centuries-long oppression of the goblins, who are denied civil rights, access to wands, and basically left with no business but to run banks (sound familiar?) and the goblins' desire for liberation, how dare they](https://gamerant.com/hogwarts-legacy-goblin-rebellion-history-lore-explained/), is only the cherry on top, as is [featuring a Jewish instrument, which just so happens to be dated in-game to the year of a real-life pogrom](https://wegotthiscovered.com/gaming/hogwarts-legacy-faces-even-more-undeniable-evidence-of-being-antisemitic-as-details-about-goblin-rebellion-match-horrifying-real-life-events/). Oh, and [did you know that Goblins believe workers should own what they produce](https://www.mugglenet.com/2019/03/the-sword-until-recently-known-as-gryffindors/)? That's right, the thinly-veiled jew-stand-ins are Marxists! You might want to look up ['Cultural Bolshevism'](https://en.wikipedia.org/wiki/Degenerate_art#Cultural_Bolshevism) (nazis today say ['Cultural Marxism'](https://en.wikipedia.org/wiki/Cultural_Marxism_conspiracy_theory)), and take a long hard look at *Deathly Hallows* again (the book). [Here is part 2…](https://eldritch.cafe/@amberage/109838270027970651)
Tomorrow’s the big day! On step closer to sunsetting everything!
Twіtter API (@fake_api)Sun, 12 Feb 2023 15:42 GMT
Always tip your software tester
Daniel Feldman (@d_feldman)Sat, 11 Feb 2023 16:37 GMT
A quick look at the history of building web apps, followed by a discussion of htmx and how it compares to both modern and traditional ways of building.

As a reminder: Fuck terfs Fuck J K Rowling Fuck that game with its antisemitism
Hughe Jazz twitter.com/modernnotoriet…Post details
The worlds largest aircraft prototype is called the Air Lander 10. The helium pumped hybrid aircraft consists of an airplane, airship and helicopter built all in one.
Modern Notoriety (@ModernNotoriety)Fri, 10 Feb 2023 03:10 GMT
Not Pokket 😈 (@NotPokket)Sun, 12 Feb 2023 07:07 GMT
Every time we drive past this shop - the Arnold Hearing Specialists - I chuckle to myself, thinking that it's capitalised as if it's being shouted at to someone who's hard of hearing 😅

Between and I took 4885 steps.
I don’t have to bother separating the art from the artist if the art sucks.
Eva (@evacide)Sat, 11 Feb 2023 21:39 GMT
Yesterday I got back from a 5-day @sourcegraph company meetup in Spain. I'm still in awe at how amazingly well-organized and produced it's been. Talks and production quality was higher than *a lot* of conferences I've been to in the past. Really cool.Thorsten Ball (@thorstenball)Sat, 11 Feb 2023 07:30 GMT
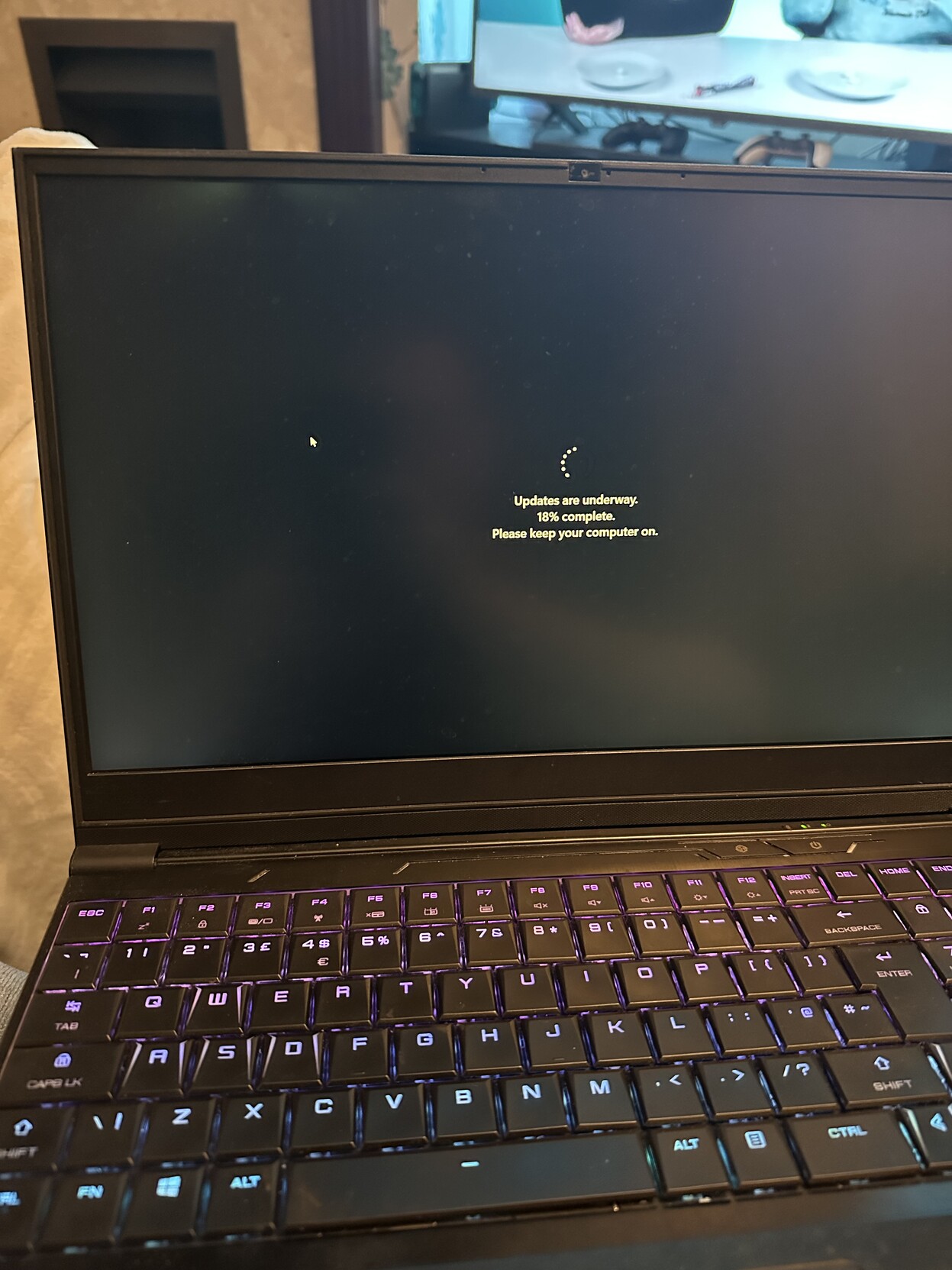
Attached: 1 image I was just in the middle of typing something and #Windows11 popped up a box about restarting for updates that stole focus. I was typing and pressing space clicked the button to restart so now I’m sat waiting for it to finish as it interrupted what I’m doing Piece of shit operating system #Microsoft #Windows #Fail #ShittyUX
Getting a GitHub App installation token on the command-line (2 mins read).
How to get a GitHub App installation token (using Typescript) for a given installation.
Passing a private key as an environment variable (1 mins read).
How to convert a PEM-encoded private key in a form to be stored in an environment variable.
I have successful replaced the majority of my body with Chinese food and shame
visual storytelling
Cloudy 🌩️ (estrogen angel) (@oncloud_e)Wed, 07 Dec 2022 20:14 GMT
*puts a collar and leash on you* LMAOO dude you just got owned 🤣
Cloudy 🌩️ (estrogen angel) (@oncloud_e)Sat, 11 Feb 2023 18:18 GMT
The interview: Spend 3 months studying algorithms to pass The job: We need a buttonRandall Kanna (Franson) (@RandallKanna)Fri, 10 Feb 2023 18:15 GMT
!!!!! twitter.com/kyliebytes/sta…
Post details
an uwu trans polyam anarchist hacking their way into the united state’s no fly list and blogging it on their super cute website at (name) dot crime dot gay is the most biblically accurate depiction of hacking that i’ve seen in the 21st century
Kylie Robison (@kyliebytes)Mon, 23 Jan 2023 16:26 GMT
Kylie Robison (@kyliebytes)Fri, 10 Feb 2023 17:14 GMT
it is extremely frustrating how inaccurately hacking is depicted in movies, never once showing hackers wearing their fursuits
April King 🌀 (@CubicleApril)Fri, 10 Feb 2023 15:22 GMT
Other than Mr Robot, which are the good hacking movies? Surely there’s something good and recent in the works? twitter.com/cubicleapril/s…Post details
it is extremely frustrating how inaccurately hacking is depicted in movies, never once showing hackers wearing their fursuits
April King 🌀 (@CubicleApril)Fri, 10 Feb 2023 15:22 GMT
jessica (@JessicaCregg)Sat, 11 Feb 2023 14:04 GMT
I’ve nominated myself as a rep for my group. I’ve no experience doing anything like this but my union told me they will help whatever way they can even though they can’t get directly involved.
My second time going through this process at Deliveroo. This time I'm in a union and I am eager to organise and help at risk workers. Fuck the profit motive. #layoffs #engineering https://www.telegraph.co.uk/business/2023/02/09/deliveroo-lays-almost-one-ten-staff-tech-job-cuts-continue/
Tfw you wish you had your own apartment so you can freely have this glass for wine based hacking depravity.
raging at injustice Abolish Qualified Immunity (@weems)Sat, 11 Feb 2023 03:31 GMT
One nice thing about organising all of the at risk Deliveroo employees and getting them onto a separate slack workspace is I've gotten to speak to hundreds of new people over the past day. More than I can say I've spoken to in the 5 years I've been with the company. #layoffs #engineering
Attached: 1 image Asda embracing polyamory with their 3 for £3 Valentine’s Day card deal

the sluttiest thing a hero can do is show up at the villain’s doorstep, bloodied and bruised, and say “I didn’t know where else to go”
chai ⵣ🇲🇦 (@proyearner)Fri, 10 Feb 2023 18:06 GMT
i want to get invited to queer kink orgies but i don't want to go to a bunch of munches and that's super unfair to me
Aster Olsen (@AsterOlsen)Fri, 10 Feb 2023 22:36 GMT