Has someone at the Linux Foundation decided they want to spam folks regardless of opting out of the "PyTorch Foundation" emails? Getting it across many more emails than I remember signing up to the Linux Foundation with, and even after unsubscribing from "PyTorch Foundation" emails, I'm now receiving them under different email events

Hi, I'm Jamie Tanna 👋🏼
If you're referring to me, I'm happy being called Jamie, Jamie Tanna, jamietanna, and that you
respect my pronouns:
he/him/his.
I'm currently a Senior Developer and Open Source project maintainer (of Renovate) at Mend.
I currently live in Nottingham with my partner Anna Dodson and our cat Morph and our dog Cookie.
I use my site as a method of blogging about my learnings, as well as sharing information about projects I have previously, or am currently, working on in my spare time.
I'm an maintainer for a number of Open Source projects, including oapi-codegen, and Renovate, as part of my job at Mend.
I'm a GNU/Linux user, a big advocate for the Free Software Movement, and the IndieWeb movement and I try to self host my own services where possible, instead of relying on other providers.
I have ADHD (Inattentive Type) and am learning how to make my life work better around it.
Due to the many social media platforms and different ways to connect, I've captured all my contact information on my /elsewhere page. Alternatively, you can drop me an email at hi@jamietanna.co.uk.
I also have a /now page which aims to cover some more up-to-date "what I'm up to" information.
Post details
Requested post by @sethmlarson: Package Managers Need to Cool Down https://nesbitt.io/2026/03/04/package-managers-need-to-cool-down.html
Post details
Sure feels like some combination of AI, the US military, and the AI military could bring an end to the world any day now, so I figured I'd better record one…

Post details
Oxide raised a truckload of capital a few weeks ago to fund the business for the foreseeable future. Bryan and Steve describe the raise, and Adam poses the best the best (and worst) questions scraped from Hacker News.In addition to Bryan Cantrill and Adam Leventhal, we were joined by Oxide CEO,...
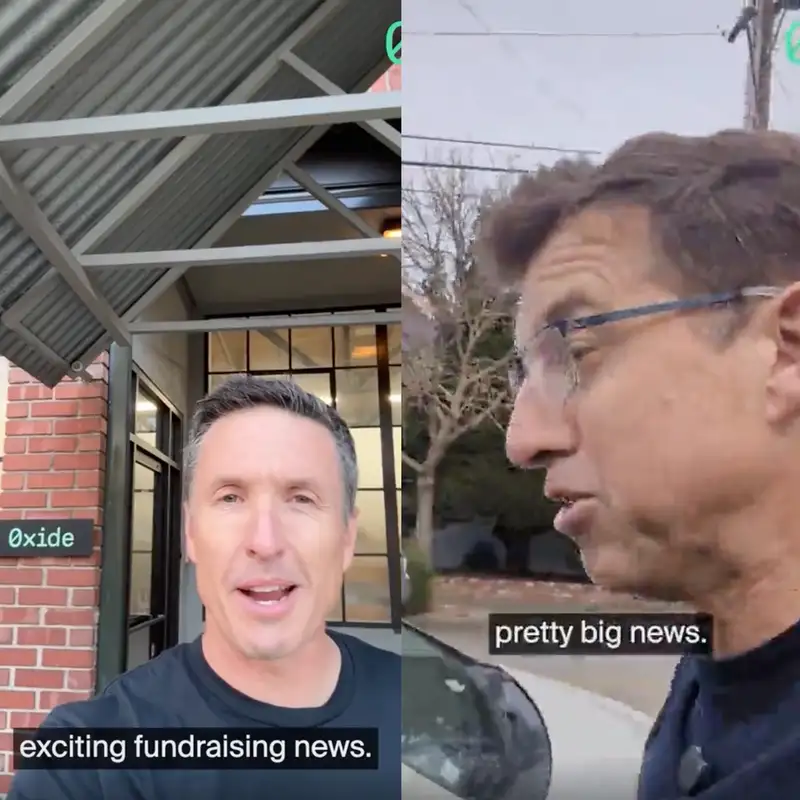
Post details
Adam and Jerod get into the news, Jerod officially retires from the pod (and Changelog), plus a bonus for our Changelog++ subs!
Does my site's analytics change how I write? (4 mins read).
Reflecting on whether how my blog is read impacts what I write.
Post details
Welcome back to Break, a Fallthrough aftershow! Kris and Matt continue the Go repository structure conversation by zooming in on the details. The pair discuss what they dislike about database libra...
Post details
Another week, another Kris & Matt duo episode! This week, we're digging into Go codebase structure, package design, and why the community keeps struggling with the same problems. The conversation s...
Week Notes 26#09 (1 mins read).
What happened in the week of 2026-02-23?
Automagically updating oapi-codegen JSON Schema version bumps with Renovate (1 mins read).

How to use Renovate to update the version pin on oapi-codegen's JSON Schema URL.
Post details
Burke Holland works on GitHub Copilot by day and codes with his AI agents always. Early January, Burke posted about how Opus 4.5 changed everything. We were all still buzzing from the holiday-season 2x usage bump Claude gave us, and Opus 4.5 felt like a genuine step function in capability. Burke and I get into all the ...
How I'm using Local Large Language Models (7 mins read).
Insight into my (low) usage of local LLMs on my personal desktop and work Mac.
Post details
🔐 Go 1.26.1 and Go 1.25.8 pre-announcement🇮🇹 GoLab 2026, Nov 1-3 @ Bologna, ItalyCFP Open through Apr 13➖ Proposal: change go mod init default go directive back to 1.N✔️ Accepted: generic methods for GoWe talked about it in E143📵 Blog: Turn Dependabot Off by Filippo Valsorda⚡️ Lightning Round🤩...

Post details
Mitchell Hashimoto on building HashiCorp, navigating the cloud giants, and how AI agents have transformed his day-to-day engineering workflow.

Automating the syncing of files between repos with Renovate and Vendir (4 mins read).

How to use Renovate and Vendir to periodically update vendored files which are out-of-sync between Git repos.
Post details
On episode 32 of Open Source Ready, Brian and John sit down with Glauber Costa to explore Turso, a Rust-based rewrite of SQLite built for the AI era.

Post details
Listen to Ep 2: Holidays from Lucy & Sam's Perfect Brains. Lucy and Sam speak to two former holiday companions to talk about the various types of medicine needed while abroad. Recorded by Aniya Das and Ben Williams, and edited by Ben Williams for Plosive. Artwork by Sam Campbell. Theme music by Paul Williams and Sam Campbell.

Post details
Listen to Ep 1: The Face from Lucy & Sam's Perfect Brains. Have you got FIRST EPISODE FEVER or what??? Lucy B and Samuel C throw caution to the wind and begin their podcast with a highly complex study of the human face. They analyze each feature in shocking depth, beginning with the bits at the top and working their way right down to the chin and they don't go off on a single tangent. Only listen to this if you are operating heavy machinery please.Recorded by Aniya Das and edited by Ben Williams for Plosive. Artwork by Sam Campbell. Theme music by Paul Williams and Sam Campbell.

Post details
Kin Lane drops by to talk to Phil Sturgeon about his new startup, the changing landscape of API tech, why REST fundamentals are still important, and building sustainable API tools.

Post details
SummaryIn this episode of the Overcommitted Podcast, hosts Brittany, Bethany, and Erika dive deep into the realities of software development with guest Robby Russell. They explore the critical challenges of maintaining legacy code and managing technical debt, emphasizing the impact on programmer productivity and long-term sustainability of software projects. Robby shares his extensive experience, including his journey creating Oh My ZSH, highlighting the importance of documentation, testing, and fostering a collaborative engineering culture. The discussion also covers balancing personal and professional commitments, an essential aspect of career growth in tech. Listeners will gain practical insights into navigating software engineering challenges while sustaining work-life balance. The episode wraps up with a fun segment on current tech obsessions from all participants.LinksPlanet Argon: https://www.planetargon.com/ Oh My Zsh: https://ohmyz.sh/ Maintainable Podcast: https://maintainable.fm/On Rails Podcast: https://onrails.buzzsprout.com/ Robby’s Blog: https://robbyonrails.com/ Robby’s Band: https://mightymissoula.com/ Commit Goods Store: commitgoods.comd’Oh My Zsh: https://medium.com/free-code-camp/d-oh-my-zsh-af99ca54212c Stop Pretending You’re the Last Developer: https://robbyonrails.com/articles/2025/07/16/stop-pretending-youre-the-last-developer/ Internal Tooling Maturity Ladder: https://robbyonrails.com/articles/2025/08/13/internal-tooling-maturity-ladder/Diataxis: https://diataxis.fr/HostsOvercommitted: https://overcommitted.devBethany Janos: https://github.com/bethanyj28Brittany Ellich: https://brittanyellich.comErika Eggemeyer: https://github.com/eggyhead

How and why I attribute LLM-derived code (9 mins read).
How I'm reducing risks of legal concerns now and in the future with AI-generated code.
Post details
SummarySean Goedecke, a staff engineer on GitHub's Copilot team and a prominent voice in software development, shares his unique frameworks for software engineering and improving programmer productivity. In this episode, discover how understanding the distinction between "pure" and "impure" engineering can impact software projects and career growth in tech. Sean breaks down the idea of "legible" vs. "illegible" work, challenges conventional approaches centered around Jira ticket queues, and discusses the evolving role of AI in software engineering. This conversation also touches on the dynamics of engineering culture and how ambitious engineers can thrive beyond typical performance metrics. Plus, Sean responds to some of his most compelling Hacker News comments live on the show, providing fresh insights into balancing productivity with impactful work.LinksSean’s website: seangoedecke.com Blog post: Pure and impure software engineering: https://www.seangoedecke.com/pure-and-impure-engineering/ Blog post: The good times in tech are over: https://www.seangoedecke.com/good-times-are-over/ Blog post: 2025 was an excellent year for this blog: https://www.seangoedecke.com/2025-wrapup/ Seeing like a state book: https://www.goodreads.com/book/show/20186.Seeing_Like_a_State HostsOvercommitted: https://overcommitted.devBethany Janos: https://github.com/bethanyj28Brittany Ellich: https://brittanyellich.comErika Eggemeyer (Eggyhead): https://github.com/eggyhead

Post details
Josh chats with Brad Axen from Block about his creation Goose as well as the Agentic AI Foundation (AAIF). I am quite skeptical of many AI claims, but Brad has a very pragmatic view about where things are today and where we might see them head. Donating Goose to the AAIF is great news as well as seeing MCP and AGENTS.MD in the foundation. We discuss how to deal with the problem of raising up junior developers, challenges of AI PRs, and some thoughts on how to get started if you're interested in AI development. The show notes and blog post for this episode can be found at

Post details
Josh chats with Brad Axen from Block about his creation Goose as well as the Agentic AI Foundation (AAIF). I am quite skeptical of many AI claims, but Brad has a very pragmatic view about where things are today and where we might see them head. Donating Goose to the AAIF is great news as well as seeing MCP and AGENTS.MD in the foundation. We discuss how to deal with the problem of raising up junior developers, challenges of AI PRs, and some thoughts on how to get started if you're interested in AI development. The show notes and blog post for this episode can be found at

Post details
Gerhard is back for Kaizen 22! We're diving deep into those pesky out-of-memory errors, analyzing our new Pipedream instance status checker, and trying to figure out why someone in Asia downloads a single episode so much.
Post details
The #Renovate maintainers would like to get some speciifc feedback on a few areas - we'd love to hear from you: https://github.com/renovatebot/renovate/discussions/41414
Week Notes 26#08 (2 mins read).
What happened in the week of 2026-02-16?
Post details
Summary:In this episode of the Overcommitted Podcast, host Bethany and co-host Brittany Ellich dive into software engineering education with Sam Rose, a developer educator at Ngrok. Sam shares his journey from software engineering to education, emphasizing his innovative approach to improving programmer productivity through visual interactive essays that simplify complex technical concepts like large language models (LLMs). He also discusses his work on prompt caching, aiming to enhance software projects by making technical knowledge more accessible to engineers and practitioners.The conversation explores Sam's unique teaching methods, focusing on visualization and interaction as key tools in software development and career growth within tech careers. Sam reflects on his transition from an engineering role to an educator, sharing insights into the challenges of this career shift, the importance of feedback, and how his personal experiences influence his work. The episode concludes with a playful segment inspired by Sam's educational approach, highlighting the integration of engineering culture with interactive learning.Tune in for an engaging discussion that blends software engineering, education, and work-life balance, offering valuable insights for anyone interested in advancing their tech career and embracing innovative learning strategies.Takeaways:"If you truly understand something and you tinker with it, the mental model you end up with should be reasonably accurate.""Don't say 25 words if you can do it in 15.""Teaching has always felt very challenging in a really privileged way."Links:Prompt caching article: https://ngrok.com/blog/prompt-caching/Bartosz Ciechanowski: https://ciechanow.ski/Load balancing article: https://samwho.dev/load-balancing/Autism diagnosis article: https://samwho.dev/blog/getting-an-autism-diagnosis/Having a baby article: https://samwho.dev/blog/having-a-baby/Write that blog article: https://writethatblog.substack.com/p/sam-rose-on-technical-blogging)The square hole girl video: https://www.youtube.com/watch?v=cUbIkNUFs-4Hosts:Overcommitted: https://overcommitted.devBethany Janos: https://github.com/bethanyj28Brittany Ellich: https://brittanyellich.com

Post details
SummaryIn this episode of the Overcommitted Podcast, hosts Jonathan, Brittany, and Erika delve into the exciting world of AI agents. They explore the potential of AI agents in software engineering, their functionality, and the challenges of building and categorizing them. The conversation also touches on the future of job searching and personal development through AI, emphasizing the need for a more personalized and effective approach to technology and learning.Takeaways- AI agents represent a new paradigm in problem-solving.- AI agents can offload cognitive tasks.- User experience with AI agents needs to be redefined.- AI agents can be tailored to specific domains for better results.- Defining success metrics is crucial when building AI agents.- Job searching processes are outdated and need innovation.- AI can assist in personal development and career growth.- Customizable search engines could enhance information retrieval.- The role of human bias in hiring processes is significant.LinksBuilding effective agentsBalanced Engineer NewsletterPlausible SchemesEmbedding modelsObsidian CopilotTech book club RepoOvercommitted DiscordHostsOvercommitted.devBrittany EllichEggyheadJonathan Tamsut

Post details

Post details
Another week, another Kris & Matt duo episode! This week, they're talking about Go. They cover the recent generic methods proposal by Robert Griesemer, results from the 2025 Go Developer Survey, so...
Post details
Visit https://cupogo.dev/ for all the links.Using go fix to modernize Go codeEric S. Raymond's tweet about auto-converting his C code to GoEric's HomepageSkill-validatorLinkedIn, GitHub, AgentSkillReport.comcmd/vet: check for missing Err calls for bufio.Scanner and sql.Rows #17747Meetups Shay...

Post details
MeetupsHello Stuttgart, 19 FebGo 1.26 is out!Go 1.26 release party with Anton ZhiyanovGo 1.26.0-1 available from MicrosoftLighting RoundBlog: Stepping out of Front-End with Go by ElGophertransition ppc64/linux (big-endian) from ELFv1 to ELFv2 in Go 1.27Discussion: Should Go accept CLs generated...

Post details
Steve Ruiz joins us for a deep-dive on tldraw (a very good free whiteboard) and the business he's built selling SDKs that help others build very good whiteboards (and more) with tldraw's high-performance web canvas. Along the way, we discuss the excitement/fear we share about keeping our agents busy, how SDK and infra...
Post details
This week it's Kris and Matt diving into the state of hardware, security, and what local AI actually needs to work. The conversation starts with AI agent social networks and why prompt injection is...
Post details
Welcome back to Break, a Fallthrough aftershow! Kris and Matt continue the hardware and AI conversation by zooming in on the tooling. Matt calls out the AI hype cycle of
Breaking free from GitHub Discussions' limitations (12 mins read).
How we built our own interface on top of GitHub Discussions to improve triage for Renovate's Open Source community.
Post details
Amal Hussein returns to tell us all about her new role at Istari, what life is like outside the web browser, how she's helping ambitious orgs in aerospace, what the SDLC looks like in 2026, and a whole lot more. Wait, moon vacuums?!
Post details
(isbn:9781979748742)GitHub Actions' required properties aren't always required (2 mins read).

A gotcha with how required: true allows an empty string as valid input.
Lessons learned from oapi-codegen's time in the GitHub Secure Open Source Fund (6 mins read).

Sharing some thoughts about the GitHub Secure Open Source Fund and how I spent the time with oapi-codegen.
Post details
Our ol' friend, Brett Cannon, is back to talk all things Python. But first! Star Wars, Machete Order, Lost, Babylon 5, Game of Thrones, Murderbot, Ted Lasso, Project Hail Mary, David Attenborough, perpetual voice rights, and the AI uncanny valley.
Post details
Paul Dix joins us to discuss the InfluxDB co-founder's journey adapting to an agentic world. Paul sent his AI coding agents on various real-world side quests and shares all his findings: what's going to prod, what's not, and why he's (at least for a bit) back to coding by hand.
Week Notes 26#07 (1 mins read).
What happened in the week of 2026-02-09?
Post details
Instead of an AI-generated hit piece, try sending your fave OSS maintainer a fun little card 💕 oss.cards https://oss.cards
Post details
Go 1.25.7 and 1.24.13 releasedUUIDs in the standard library?crypto/uuid: add API to generate and parse UUIDscrypto/rand: add UUIDv4 and UUIDv7 generatorsThe most popular Go dependency is...Lightning roundRust vs Go in 2026 by John ArundelWelcome to Gas Town by Steve YeggeInterview with Jakub...

Post details
Welcome back to Break, a Fallthrough aftershow! Kris, Matt, and Steve pick up where the main episode left off, asking whether copyright actually matters to working developers. Kris draws parallels ...
Post details
me at 17: a secret conspiracy of billionaires shapes global events me at 35: class interest creates emergent outcomes and aligned behavior, but there’s no smoky room where plutocrats plot to shape global events me at 41: a secret conspiracy of billionaire perverts shapes global events [contains quote post or other embedded content]
You're currently viewing page 1 of 173, of 8634 posts.
